| | | Cyber Defense Awareness Team | | The Cyber-Tooth Times |
|
|
|  |
| | | Message from Maritsa: New Year, New Programs |
| | 
| Maritsa Santiago
Sr. Director, Information
Security Awareness | This month, communications regarding updates to our phishing simulation and compliance training processes were distributed. Please ensure you carefully review each to understand the potential counseling and/or disciplinary actions involved with continuous failures of simulated phishing emails or incompletion of training by the assigned due date.
The intent of each is not to penalize staff, but to highlight the importance of personal accountability for compliance and security, no matter your job role in the organization. We are all human and prone to making mistakes from time to time. With this understanding, we built in opportunities to educate and aid those who continuously fail to better understand their accountability, which we hope will, ultimately, reduce the overall security risk for our staff, customers and stakeholders.
With the education and training provided, I hope that you take the opportunity to learn and apply best practices for both your home and work lives.
 If you have questions not addressed in the FAQs, please reach out to the Cyber Defense Awareness Team or Regulatory Compliance Group - we’re here to help. If you have questions not addressed in the FAQs, please reach out to the Cyber Defense Awareness Team or Regulatory Compliance Group - we’re here to help. | |
|
| | |
| |
| Protect Yourself from Ransomware |

Ransomware is a type of malware, or “malicious software,” that threatens to publish victims’ data, or block access to it, unless a ransom is paid. If executed correctly, it can hold cities and organizations hostage for extended periods of time. Phishing is the most commonly used method of delivery, which is why our organization focuses heavily on educating staff on the importance of recognizing and reporting a phish.
Signs you have suffered a ransomware attack:
- Pop-up messages requesting funds or payment to unlock files
- Inability to access your devices
- Login doesn’t work for unknown reasons
- Files unexpectedly request a password or code to access them
Thankfully, you’re not helpless against ransomware. Read and remember these tips:
- “Paws Before You Pounce” on emails: Avoid phishing scams that spread ransomware by not clicking suspicious links.
- Be cautious of suspicious websites: “https:” (vs. “http:”) in your URL, or website link, indicates information entered into a website is encrypted. However, don’t assume all https: sites are secure. Be vigilant to only visit legit, known sites.
- Be cautious of public Wi-Fi: Connecting to unsecured Wi-Fi opens doors a cybercriminal can walk through. Use a VPN service or utilize your phone data for more security.
- Back up your devices regularly: For your home security, be sure to back up your computer and mobile devices, plus, always use up-to-date internet security software. There are several ways to back up devices: external hard drives, cloud backup, flash drives and back-up services are a few. For more information, see this Norton site.
With the help of everyone, we can feel better knowing how to recognize and protect against ransomware attacks.
|
|
|

As Lexi says, “Paws Before you Pounce,” on each and every email you receive. When you think an email could be malicious, it is critical to use the “Report Phishing" button so that the Security Operations Center (SOC) can determine whether the email is malicious and, if so, take necessary remediation steps.
We'd like to reward our recent fastest phishing simulation reporters with a $25 (or country equivalent) Amazon voucher. A big THANKS and congratulations to:
Nicole Little, Boca Raton
Kelly Ilustrisimo, Minneapolis
Pia Foulkes, London
Has your Report Phishing button disappeared? Have no fear, reinstallation instructions are here. If on a Mac or mobile device, please forward the email as an attachment to security@lexisnexisrisk.com. |
|
|
 |
| Naughty and Nice - Avoid Security Pitfalls |
 In this edition, we are spotlighting two security pitfalls to avoid—sent by our astute, security-minded readers. In this edition, we are spotlighting two security pitfalls to avoid—sent by our astute, security-minded readers.
Krista Palframan alerted us of instances where data was inadvertently sent to incorrect vendors when Outlook’s Auto-Complete for recipients was employed. Avoid this dangerous pitfall by turning off Auto-Complete or ALWAYS reviewing each recipient for appropriateness before sending (Pawsing Before You Pounce). To turn off Auto-Complete in Outlook, navigate to File > Options > Mail > and Uncheck the “Use Auto-Complete List...” option. Thanks for bringing this to our attention, Krista!
Another employee received a call through MS Teams from a vendor asking to speak with our CTO, Vijay Raghavan. Once the call was transferred to Vijay, it appeared to come directly from the employee instead of an outside entity. That false appearance could easily become a social engineering threat. If you need to transfer a Teams call, select the “ring back if there is no answer” setting, which will send the call back to you if the colleague doesn’t answer. Additionally, consult with the colleague the call is being transferred to before transferring, to provide the caller’s details. Refer to the Microsoft Teams Call Transfer instructions on our FAQs. Thank you, Chris Beaver, for creating the helpful Teams instructional.
We should always be thinking of new ways to improve our security culture, and sincerely appreciate these contributions. Submit  your ideas for improvements to Cyber-Tooth Lexi. Please report actual or potential security issues to security@lexisnexisrisk.com right away. your ideas for improvements to Cyber-Tooth Lexi. Please report actual or potential security issues to security@lexisnexisrisk.com right away. |
|
|
 |
| Security Tip: Vendor Relationship Best Practices |
Many of us could be conversing with vendors to review or initiate business relationships in the new year. Follow these best practives and do not divulge senstive company information when corresponding with vendors: - Remember, a vendor's first goal is to generate revenue.
- Seemingly harmless comments about project status, recruitment plans or other company endeavors may compromise our security.
- Information that we learn from one vendor should never be shared with a different vendor. Besides potentially breaching non-disclosure agreements and contracts, it may break the law.
- Inform vendors that attempt to draw sensitive company information from you that this behavior may result with them being prohibited from further company engagement.
In summary, friendly conversations and interactions with vendors are fine, but divulging sensitive information is not. For more information, visit the RELX Third-Party Service Security Management Program. |
|
|
 |
| Data Handling Reminders on SharePoint |
| Our business is data, and protecting the data we store, transmit and process is of paramount importance—not only to meet regulatory requirements, but also because we owe it to ourselves and clients. To help you, we created a new SharePoint page with comprehensive information and resources for categorizing, classifying, storing and transferring data. Please visit and bookmark it for future reference. This handy IVC infographic succinctly summarizes our data classification types and how to secure them in transit and at rest. Please reach out if you need additional guidance. 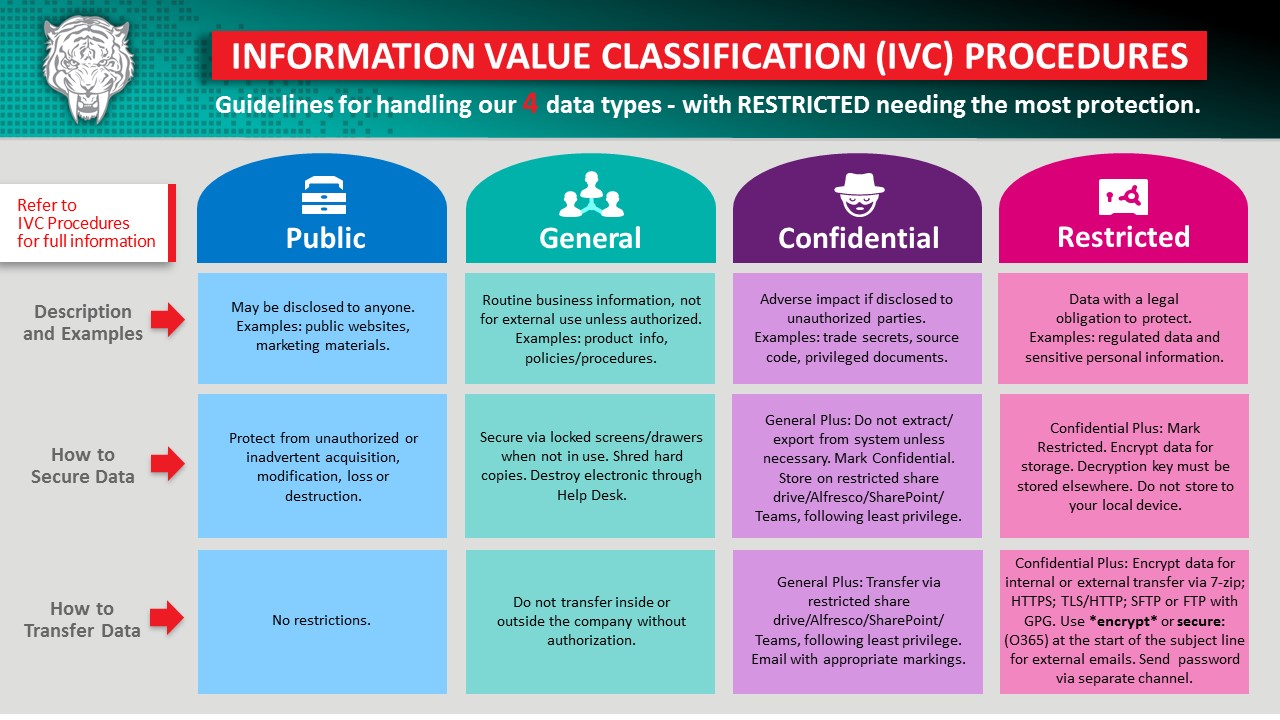
Click to see full size image  |
|
|
| Did you find this newsletter useful? |   |
|
|
| YOU Could Be an RSG Security Champion! | 
Do you find the world of cybersecurity fascinating? Would you like to help keep our company safe from cyber threats? Does impressing your friends and peers, by being a subject matter expert in this exciting field, interest you? If “Yes" to any of these questions, apply to become an RSG Business or Technology Security Champion!
Here is all you need to know about becoming an extension of the Cyber Defense Awareness Team.

|
|
| Read the Cyber-Tooth Times and Win! | | We want you to enjoy all the content in The Cyber-Tooth Times. Therefore, we offer an incentive to read it all the way through. Whenever you see Lexi's paw in the newsletter, click, or "pounce," on it. You'll then be taken to a question, answer it correctly to be entered to win $25 (or country equivalent). 
The more you pounce, the better your chance to win! Congratulations to last quarter’s winning pouncers:
Jason Gray, Indiana
Angeline Wong, Pittsburgh
Katherine Henderson, Ithaca
|
|
| Who's Who in InfoSec |

Alain Tass
Security Engineering Lead, Red Team
Tell us a bit about yourself.
I joined the Emailage InfoSec team about two years ago. I've always been into ethical hacking but didn’t work in the field until I moved to Ireland seven years ago. Now, I've joined the Red Team at RSG. The purpose of this team is to identify security weaknesses in business processes by demonstrating real world attacks. I am excited about it and have big plans!
What does a typical day look like for you?
As I'm transitioning into the Red Team, I still work on application security processes, vulnerability management and penetration testing at Emailage. With the Red Team, I am also working on creating new processes and building team exercises.
Where do you live? Do you have any hobbies?
My wife and I live near the Wicklow mountains in Ireland. It's a beautiful place! That's where they filmed the tv show, Vikings. I have the opportunity to go hiking all the time.
My hobbies are technology (obviously), pets, Japanese anime, music, reading, listening to business and finance podcasts, bug bounties, meditation, working out and nunchucks. My interests are always expanding. 
|
|
| Lexi's Security Toolkits | 
With security threats growing exponentially from year to year, we must be up to speed on our security policies, resources and best practices.
Luckily, we've made it easy for you to learn more. Simply choose a presentation topic from our Security Toolkits folder and incorporate any of the included resources in your next meeting. With the slides, videos and notes (complete with tips!), you'll look like a cybersecurity pro.
Our team would love to virtually attend your meetings with guidance specific to your audience. Contact us with your needs!
|
|
| In Case You Missed It - Lexi Presents | |
|
|
| | |
|
